Cloud-Based Software Backed By Cybersecurity Accelerates Essential Work
By Colter Cookson
The growing popularity of remote work has motivated hackers to target corporate clouds, business insurance provider Hiscox warns in an August report on cybersecurity readiness across sectors. Forty-one percent of the cybersecurity professionals surveyed for the report identified cloud servers as the entry point for an attack they had experienced.
“The main way in for hackers is corporate servers, and there has been a big jump in the numbers reporting entry by cloud server,” the report reads. “This aligns with the warning from international agencies that bad actors are increasingly targeting cloud infrastructure.”
But attacks on the energy industry fell sharply between 2021 and 2022. While the report does not speculate on the cause, it’s possible the 2021 ransomware attack that temporarily shut down the Colonial Pipeline spurred energy firms to strengthen their defenses and made them less attractive targets.
The oil and gas industry always has been aware of the risks associated with cloud platforms, says Vince Dawkins, chief executive officer of Enertia Software. “When customers look at our cloud software, they always ask how we will keep their data safe,” he reports. “However, the industry’s comfort level with the cloud has risen tremendously as the big boys–Microsoft, Amazon and Google–have taken ownership of cloud infrastructure, anchored the technology and invested heavily in its security.”
Strong cybersecurity still requires effort from software providers and end users, but the more secure underlying infrastructure has lowered the barrier to entry. “We have quite a few customers who are asking us to move from an on-premises solution to a software-as-a-service solution,” Dawkins reports. “We see SaaS as the wave of the future, one that will enable customers to spend less on IT but still get the best software.”
Moving to the cloud has given Enertia a chance to reimagine its interface, Dawkins comments. “We are asking our user base what we should change or evolve, then testing and implementing those changes as fast as we can,” he says. “As we improve the interface, our top priority is making it as efficient as possible for users to achieve their goals.”
That means making it obvious to users how to complete their tasks, Dawkins outlines. He says the company designs interfaces so the most common tasks can be performed in a few simple steps, with other capabilities available but hidden until they are needed.
Alongside improvements to programming tools and crowd sourcing techniques, the industry’s migration to the cloud is helping software providers quickly create, test and deploy new features or enhancements. Enertia Software points out that these improvements are guided by explicit customer feedback, as well as subtler indicators of need, such as common support questions.
Enertia is trying to simplify tedious work, Dawkins adds. “For example, we have a tool for updating ownership information that previously required users to make changes one at a time,” he says. “Today, users can make mass changes to a deck or an asset’s ownership information, which saves a lot of time.”
Accelerating Improvements
Feedback drives improvements to Enertia’s software, Dawkins assures. “We ask customers what will benefit them not just internally, but also with the help of an external group,” he says. “We also monitor the questions for our support department to see if the same questions have been asked frequently across the industry or at a specific company.
“If we see the same question from several people at an organization, we will reach out to the company to see what it is trying to get out of the software and figure out how we can help,” he says. “Sometimes that is as simple as walking its people through the steps on the phone or providing more formal training. In other situations, we will look at specific development.”
The cloud has made it easier for software providers to roll out updates, which can be useful when regulations change and processes need to be updated, Dawkins notes. He emphasizes that the company takes a deliberate approach to updates and tests each thoroughly.
“I expect the rate at which companies adopt and improve technology to speed up,” Dawkins predicts. “Open-source development and crowdsourcing help with that. Sometimes we can solve a problem by putting it out there, letting thousands of developers grapple with it, and taking the best solution.”
Automating Processes
The labor market is tight, observes Brent J. Rhymes, chief executive officer of PakEnergy. “The oil and gas industry may be facing particularly acute labor shortages because it has fallen out of favor with many young people,” he assesses. “This situation has companies looking to do more with less, and one of the best ways to achieve that goal is automating processes.”
Automating the flow of information from the field to the back office has reached a point in which companies of all sizes can manage it, Rhymes reports. “We have seen everyone from small ‘mom and pop’ companies or startups with a few wells to publicly-traded independents with thousands of wells migrate to our integrated suite of oil and gas, cloud-based business automation solutions,” he illustrates. “They all want to make their operations as efficient as possible.”
PakEnergy says it is augmenting its integrated land, production, accounting and transportation platform by introducing a business intelligence package. The company adds that it is creating a secure network for exchanging documents, such as invoices and division order letters, with vendors, landowners and other stakeholders.
Rhymes says one of the biggest efficiency gains occurs in owner relations. “Most companies still manage owner relations using inefficient paper or email-based processes,” he says. “They will either maintain an internal owner relations help desk or contract with a third party to provide that help desk, which fields calls from owners about their royalty statements. When these companies need to update division orders, they mail out letters and wait for owners to sign and return them.
“Our new digital owner relations management portal gives companies the ability to automatically publish documents from the integrated suite’s land management product to owners through a secure portal,” Rhymes contrasts. “When new statements are available, we notify owners by email. The portal answers many of their most common questions, cutting down on the number of incoming help desk calls.”
Rhymes adds that the platform supports e-signatures, which means companies can get signatures for new division order letters without relying on snail mail. “For some of our larger customers, the savings on postage alone are significant enough to offset the cost of the software,” he reports. “At the same time, the owner has a better experience. They can log in to the portal and get their latest statement whenever they like.”
Simplifying Exchanges
The owner relations portal is part of a broader document exchange that Rhymes credits with streamlining interactions between operators and their vendors, investors and partners.
“To make it easy for companies across the industry to exchange documents, we are creating a network of operators, first purchasers, service companies, investors and vendors that is modeled after social media,” Rhymes outlines. “Once a company joins the exchange network, they can exchange invoices with any vendor that is on the network.”
Commercial tools already allow companies to issue invoices, track their progress through each step in the customer’s approval process and receive notifications when the invoice is paid, Rhymes acknowledges. “The challenge with these legacy solutions is setting up connections between customers and vendors,” he says. “To bring on a potential customer, the vendor has to create a link between its ERP system and the customer’s, which sometimes takes weeks.”
With the new approach, that integration process is as straightforward as sending a friend request to a company, or if it is not already on the network, inviting it to join. “The invites are like the ones from LinkedIn,” Rhymes describes. “The recipient gets an email with a link, clicks it and sets up a profile, which only takes five minutes.”
One of the network’s early adopters is Lea Ann Stevenson of TYGR Operating Co., an independent based in Shreveport, La. “PakEnergy has cut my time processing and paying vendor invoices by around 60%,” she says.
Rhymes says the exchange supports more than invoices; it can be used for securely sending or signing other documents, such as division orders, run statements, owner statements, 1099s, W9s, insurance certificates, ACH forms and change of address forms.
Business Intelligence
To simplify decision-making, many companies are looking for ways to break down data silos and transform complex data into informative graphs, Rhymes says. “We know such business intelligence matters because we have seen smart companies spend thousands or millions hiring BI consultants to cobble tools together in their own environment,” he comments. “Many of these companies did a great job and now have access to sophisticated reports and graphs.
“But developing internal systems is too expensive for most of the market,” Rhymes assesses. “To make BI more affordable, we have developed an off-the-shelf analytics package that is easy to set up but flexible and intuitive enough to appeal to companies that want to build their own reports.”
As part of PakEnergy’s integrated platform, Rhymes says this intelligence package can access data from several departments, including land, production, accounting and transportation. “There are lots of use cases,” he reports. “For example, operators can track wells’ profitability as oil quality varies. Our first purchasers can link the package with our exchange system and monitor vendors’ costs and performance to identify the ones that provide the most value.”
PakEnergy takes cybersecurity very seriously, Rhymes assures. “We have a tight partnership with a security firm that does all our testing. We do formal annual reviews as part of maintaining our cybersecurity certifications. And we monitor our environment closely and conduct quarterly reviews,” he relates.
Rhymes adds that the company is certifying that all its products meet SOC 2, a standard developed by the American Institute of Certified Public Accountants that governs how cloud-based companies manage and protect data. “We expect getting the certifications to take nine to 12 months,” he says. “The products that have not yet demonstrated SOC 2 compliance still follow the associated procedures.”
In general, Rhymes says cloud-based services will be more secure than internal infrastructure. “Several of our clients were breached because of issues they missed,” he says. “For these companies, providing and securing computing infrastructure was a necessary evil. For a software developer, it is part of our core business.”
Why Cybersecurity Matters
When oil prices rise, it has ripple effects throughout the economy, observes John Lundgren, who spent 15 years in cybersecurity with the U.S. Navy before co-founding BreachBits in 2018 with fellow cyberwarfare veteran J. Foster Davis. “Given how much disrupting oil supplies affects our economy, oil and gas companies can be an attractive target for politically-motivated hackers,” he says.
Other cybercriminals primarily seek financial gain, Lundgren describes. “Like any commercial enterprise, the financially-motivated actors want to be as efficient as possible,” he says. “They search for targets of opportunity who can offer a quick return on investment, such as companies with exposed passwords and vulnerable infrastructure.”
But even money-oriented hackers will go after specific companies that seem likely to pay a large ransom, Lundgren warns. “To identify these companies, attackers scan press releases for news of large investments or acquisitions. They see capital infusions as a signal the company can withstand an attack and pay a large ransom.”
As oil and gas companies digitize, integrate and automate more business functions, their cyber-risks may increase, Lundgren says. “However, we have seen companies in the upstream, midstream and downstream segments of the energy industry deploy automation while maintaining strong cybersecurity,” he assures.
Lundgren cites a report BreachBits published earlier this year after assessing 98 energy companies’ vulnerability to attacks using automated tools. While every sector had companies at high risk, 41% of the firms analyzed had low or very low risks.
With automated tools, BreachBits says it can probe upstream, midstream and downstream companies’ digital infrastructure for unpatched software, easily-guessed passwords, configuration issues and other weaknesses hackers exploit. When paired with the right culture, such testing can help companies deter hackers and respond quickly to any attacks that still occur.
“Successful companies tend to think about cybersecurity as they are digitizing processes rather than trying to bolt it on afterward,” Lundgren advises. “They ask how an attacker can take advantage of their digital infrastructure, then put controls in place to prevent or mitigate those attacks. For example, they may set up guardrails that issue alarms if a system begins operating outside expected parameters so the company can fix the issue or take the system off line.”
It’s important to have enough visibility into newly automated infrastructure to identify potential attacks, Lundgren says. He recommends that companies think about how they should respond to attacks ahead of time and rehearse those processes.
Culture’s Role
According to Lundgren, the most resilient organizations embrace self-reflection. “These organizations’ senior leaders realize cybercriminals have time and resources on their side and understand that even the best companies cannot become completely safe,” he says. “Instead of getting angry and asking who needs to be fired when someone discovers a weakness, they celebrate the discovery and act on it.”
To help companies find those weaknesses, Lundgren says BreachBits has developed tools that automatically search for ways attackers can gain access to a company’s systems or data. These threat vectors often come from vulnerabilities in software; weak, reused or exposed passwords; and configuration errors.
“While attacks based on vulnerabilities remain common, they have become less frequent as companies have gotten more diligent about patching software,” Lundgren observes. “However, attacks that exploit weak credentials have risen. It is dangerous to rely on a user name and password as the sole means of authenticating someone.”
Multifactor authentication has such an outsize chance of thwarting attacks that Lundgren suggests implementing it wherever possible. “When MFA is not in place, companies should have an honest discussion about what makes it impractical and what else they can do to mitigate their risks,” he urges.
Configuration issues also can expose companies’ data. “For example, sometimes our customers upload files to cloud resources that are configured to be public,” he illustrates. “If attackers can steal an organization’s sensitive data without breaking into its system, the company may be subject to ransom demands.”
Frequent testing is vital to enforcing best practices and keeping pace with changes in digital infrastructure and cybercriminals’ techniques, Lundgren advises. “With automated assessments, we can look for threat vectors continuously, weekly, monthly or at whatever cadence makes sense for the organization,” he says. “Once testing has identified and confirmed the potential threat vectors, organizations can decide how to respond. Usually, organizations start by addressing the vectors that have the highest impact potential and likelihood of being exploited.”
When companies evaluate the risks associated with each threat vector, they need to involve representatives from across the business. “If people from IT are the only ones in the room, they sometimes incorrectly assume that disrupting a particular piece of software will have a minor impact,” he explains. “The owner of that software is in a much better position to describe how a disruption would impact the overall organization.”
Because so many attacks on operational technology originate in the information technology environment, Lundgren says a company with a well-protected IT environment can reduce OT infrastructure’s exposure significantly.
Protecting OT From IT
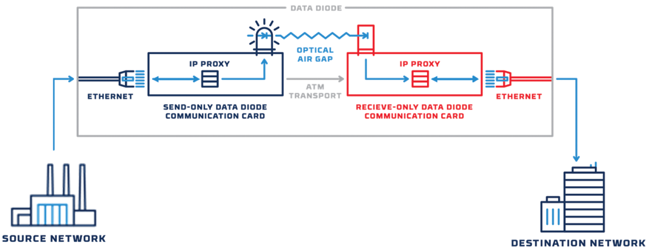
In many facilities, operational technology is isolated from the IT environment through air gapping. In other words, the equipment is not connected physically or digitally to the company’s IT infrastructure, notes Ron Brown, senior solutions engineer at Owl Cyber Defense.
One-way data diodes enable companies to get information from critical infrastructure without exposing that infrastructure to infection from the less secure information technology environment, Owl Cyber Defense says. The company explains that the diodes transmit data using light that only the IT network has the hardware to interpret. This makes it physically impossible for the diodes to send data the other way.
“In some especially sensitive applications, air-gapping will continue to be used,” he assesses. “But as oil and gas companies try to become more efficient, many are closing air gaps to gain real-time visibility into their facilities’ operations and easier access to data. Unfortunately, this IT/OT convergence may allow malicious software to migrate from IT systems to OT equipment.”
Although firewalls can provide some protection to critical OT infrastructure, Brown cautions that they can be unreliable. “As software, firewalls can be bypassed if they are improperly configured or if they have an unpatched vulnerability,” he explains.
Instead, Brown recommends using data diodes, physical hardware that only allows information to move in one direction. “With a data diode, it is impossible for any data to travel from the less secure IT network to the OT system unless a second, separate diode connection is set up,” he emphasizes. “This hardware-based approach offers such high protection to critical equipment that it is widely applied in sensitive government systems and the nuclear industry.”
For other great articles about exploration, drilling, completions and production, subscribe to The American Oil & Gas Reporter and bookmark www.aogr.com.