Cyber Security
Proactive Measures Mitigate Critical Cyber Security Challenges
By James Clark And Geoffrey Graham
BOSTON–At the heart of every oil and gas company are industrial control systems (ICSs) and other operational technologies (OTs) designed to efficiently, reliably and safely process the extraction, refinement and distribution of large quantities of fuel needed to keep global economies moving.
While OT systems once were seen as immune to cyber security threats because of their separation from corporate information technology, this approach is no longer realistic in today’s interconnected world. Malware and cyber attacks are posing new threats across the industry, and are exposing weaknesses in ICS and OT designs, putting the production, reputation and profits of critical energy providers at risk.
All around the world, security officials are upgrading cyber defenses to ensure intelligent protection for critical infrastructure is in place. In many cases, organizations are employing an array of IT security technologies such as firewalls, and anti-virus, intrusion-detection and prevention systems. While this is an important sign that the threat is being taken seriously, these measures are falling short of delivering the protection ICSs and OTs need.
The Threat
In 2012, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team responded to approximately 200 cyber incidents reported by energy companies, public water districts, and other infrastructure facilities. More than 40 percent of those attacks were believed to have targeted the energy sector directly. The type and severity of these threats can vary from conventional malware, spam and phishing attacks to highly targeted, advanced persistent threats and nation-state sponsored activities.
These threats manifest in a number of ways. One of the most common attacks involves spear phishing e-mail campaigns. These attacks utilize e-mails that contain malicious content and are sent directly to the accounts of energy industry and oil and gas company employees. All it takes is one employee opening an e-mail to compromise the network.
It was suspected that several other security incidents were triggered by employees at oil and gas companies accidentally uploading malware into their own networks by using contaminated portable media devices.
While implementing strong IT security policies helps mitigate some of these risks, it’s nearly impossible to eliminate all instances of operator error. Historically, these attacks targeted IT systems, and malware could move from IT to OT systems.
While spear phishing attacks are the most common, it is the threat of malware or targeted cyber attacks to an OT system that is of greatest concern. The more exposed to external systems and the outside world an industrial control system becomes, the higher the risk and the greater the threat. In addition, there is a significant risk of an individual with “insider” knowledge using his skills to manipulate a system to detrimental effect, or of a process error or unintentional numerical error propagating through a system and causing damage.
Need New Solutions
In 2012, the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team responded to approximately 200 cyber incidents reported by energy companies, public water districts, and other infrastructure facilities. The type and severity of these attacks can vary from conventional malware, spam and phishing attacks to highly targeted, advanced persistent threats and nation-state sponsored activities
Historically, separating critical industrial networks from corporate IT using an “air gap” has been the security method of choice for OT operators. However, numerous incidents and studies have shown that air gap security is an illusion.
An OT network is almost never completely isolated from the business network, nor the Internet. For example, OT equipment carries software that needs updating. Despite the security risk, these updates often come by way of software carried from the corporate network or a contractor’s network through a USB drive.
Driven by a desire to improve efficiency, enhance productivity and lower costs, the continued industry push for process automation and enhancing both human and machine connectivity is driving many in the oil and gas industry to seek even greater convergence of their IT and OT networks. Such convergence mandates new security solutions capable of addressing the new security threats this introduces.
Any network with a link to the outside world can provide an open door for bad actors that have the right skills, resources and knowledge to take control of components of OTs and ICSs, issue false commands, send false datasets, etc. It also provides a channel for malware to enter the organization and spread throughout the network, either carrying out actions independently, or reaching back to a malicious command and control infrastructure.
Defense In Depth
One lesson learned from the IT environment is that no single security solution can provide peace of mind.
IT network security has adopted the concept of “defense in depth,” where multiple layers of security are placed throughout the network environment. This approach defends against attacks using multiple independent methods. The defense-in-depth approach seeks to not only prevent security breaches, but also to provide an organization time to detect and respond to intrusions, thereby minimizing the potential impact.
Every ICS environment is different. There is no “one size fits all” solution. Traditional forms of security aim to identify, block, or remediate cyber risks before any damage is done. However, as cyber attackers have become more skillful, the ability to identify and stop a virus before it enters the network is no longer enough.
Increasingly, cyber attacks consist of a series of seemingly unrelated events that are deliberately conducted over an extended period so as not to raise suspicion. Defense in depth allied with monitoring that is capable of identifying these behaviors provides intelligent protection against these types of advanced attacks.
To enhance the effectiveness of security products, many organizations deploy a variety of layered solutions in different configurations. For example, four types of security solutions that can form the backbone of any defense-in-depth strategy within OT are:
- Externalized cloud Web browsers,
- Data diodes;
- Firewalls; and
- Network segmentation appliances.
To ensure these systems are aligned properly with the security needs of the business, consistent data monitoring also must be in place.
Externalizing Web Access
Since most malware and cyber attacks are caused by access to the Internet, securing the enterprise network would be fundamentally easier if Web connectivity was not required. However, few security managers would be prepared to recommend a complete block on Web access.
To solve this problem, a new form of Internet gateway has been developed that effectively externalizes Web browsing to the cloud. Using this solution, Web connectivity can be provided through an externally hosted, virtualized, secure browser. This solution can protect comprehensively against infiltration, and malicious command and control attempts.
When Internet access is externalized, Web-based threats can no longer infiltrate the enterprise network. Web users may trigger and install drive-by downloads and other exploits, but the attacks would be constrained to the cloud-based Web sandbox, which would, in response, be repaired rapidly by reverting to clean, virtual machine images. Malware that does make its way into the enterprise network–by way of e-mail, USB sticks, or other means–would be unable to communicate easily through the Web back to its controllers.
Data Diodes And Firewalls
A data diode is a simple segmentation device and highly effective security tool, when deployed correctly in high-security environments. As a unidirectional gateway, a diode will pass information in only one direction. Since data diodes are a hardware solution, their one-way enforcement cannot be compromised by online software attacks and infiltration of malware.
A key benefit of a diode is that it gives very high assurance for the confidentiality of the destination system, which is more important in OT environments. Diodes also protect the operation and data integrity of the source system from attacks originating in the destination. This makes them ideal for monitoring systems remotely without risk of compromise from the remote system.
Although using diodes is attractive because of their simplicity and lower costs compared with other solutions, one must consider carefully whether a unidirectional data flow is truly appropriate. For example, in cases where remote access and configuration management are desired, a segmentation appliance might be the better option.
A firewall implements a set of network traffic rules based on either the metadata associated with each network traffic packet, or in more advanced systems, by checking the contents of each packet against a set of known bad signatures. This can effectively prevent obvious or known attacks at the network perimeter.
Until a few years ago, very few viruses and malware were designed specifically for OT environments. Now, ICS networks are a significant target for cyber criminals and other sophisticated groups. The newest ICS firewalls support a variety of protocols, and are easy to configure to add content-based rules and policies for any proprietary protocols and protocol variations.
Next-generation firewalls also offer deep content inspection–a form of network filtering that examines an entire file as it passes an inspection point, searching for any known viruses or malware.
Firewalls can be a relatively inexpensive security solution. They are ubiquitous, and most are designed to be used in a wide range of situations to prevent malicious intrusion. However, oil and gas companies cannot rely on traditional firewalls alone because they can prevent only known, identified attack vectors, commonly understood as blacklisting.
It would be impossible for most IT network managers to enumerate and define the content of all the types of data exchanged. This makes blacklisting, the access process that denies network entry to recognized attackers, preferable to white-listing, which ensures only approved communications go through the network.
In an OT network, the types and volumes of data exchanged are much smaller. Therefore, white-listing, which is a proactive security solution, is ideal because it protects against new and unknown (sometimes referred to as “zero-day”) threats. With white-listing, blocking zero-day attacks can be achieved by permitting only known and validated communications to flow. This approach helps to “future proof” the converged network, giving security managers the flexibility to white-list anything they want to allow through.
Network Segmentation
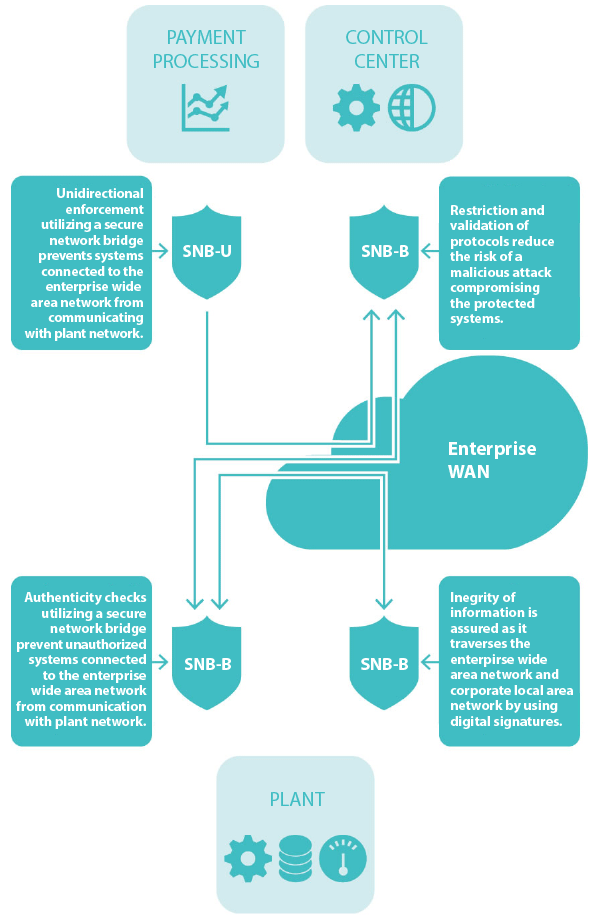
An important feature of a data bridge is that the security functions are implemented in hardware, which offers significantly better protection against software attacks. These security functions assure communications between the bridges resist many types of cyber attacks, including man-in-the-middle and malicious content-injection attacks, which are common attack vectors for this type of system.
An important step in defending a converged IT and OT network is, on the one hand, to ensure that where appropriate, segmentation continues to be enforced between different parts of the network. This ensures high-risk activities are isolated from high-value assets within operational technologies.
On the other hand, it is also important to ensure that where needed, data may flow between network segments, and the exchange will be performed securely and be tightly controlled.
Network segmentation appliances usually offer additional features than do firewalls or diodes. They combine the additional security of a hardware-based solution with the assurance that the integrity and security of communications sent between the segments are protected. They also may have differing deployment architectures to enable these features, such as a data bridge.
A data bridge is designed to control the data transferred between boundaries separated by a less trusted network zone, which ensures that communications are authentic and authorized at the point of entry into the protected segments.
A typical configuration for these appliances consists of a transmitting appliance and a receiving bridge that span the converged network. The transmitting bridge accepts data from within the source network, validates the data according to white-listing rules, digitally signs them, and converts them into a unique protocol for transmitting across the converged network.
When the data are transmitted between network segments, the recipient bridge unpacks the data, inspects them to ensure they are from a known source, and checks that the data have not been changed in any way since leaving that source. Then, once again, the data bridge verifies that the information conforms to white-listing rules before forwarding the data within the network.
An additional component in the makeup of these bridges is technology that provides the flexibility of both uni- and bidirectional automated data exchange, as required.
Performing these security logic functions in hardware–not software–makes it more difficult for an attacker to find, let alone attack, the appliance on the network (as well as the OT network on the other side of it). It also assures that communications are resistant to many types of cyber attacks, including man-in-the-middle and malicious-content injection attacks.
Monitoring And Test Beds
With the convergence of OT and IT, the importance of monitoring is twofold. First, there is the requirement to monitor the enterprise local area network. This provides a better understanding of what is happening within the enterprise, with a goal of mitigating risk and preventing cyber attacks or malware from spreading into the supervisory networks, ICS, and industrial processes.
Second, monitoring the supervisory networks, OT and industrial processes safeguards those networks from attack and mitigates the spread of any attack to the enterprise.
Organizations today can no longer look only for malware. It is crucial to seek the behaviors, data or indicators that are representative of malicious intent.
Effective defense-in-depth solutions require experimentation, and combining products in different ways and at different points of the network. As new security technologies are developed, or new combinations of security products are considered, ICS security managers need a way to test these products without compromising highly valuable OT.
Cyber test beds are another element of traditional IT security that should be adopted for OT environments. A cyber test bed is a rapidly configurable environment that can mimic a variety of ICSs. A test bed can help achieve five goals:
- Provide assurance for mission-critical functions;
- Ensure systems will satisfy safety and reliability requirements;
- Provide assurance the system will support scalability and adaptability demands;
- Allow IT managers to analyze their systems for vulnerabilities to offensive cyber operations; and
- Enable managers to test essential software patches within restricted environments before deploying them in live networks.
A robust ICS cyber test bed allows security managers to deploy and test multiple iterations of defense-in-depth solutions, testing both their robustness and cost effectiveness, while also confirming compatibility between the solutions and operational technologies before scaling the system across the entire OT environment.
Conclusion
The world has entered an age in which well-organized and well-funded groups use sophisticated cyber techniques to attack oil and gas companies with increasing frequency.
This threat landscape is constantly changing, and modern cyber defenses must evolve with it, even more quickly. While it is not always possible to map IT security solutions directly into ICS and OT networks, there are a range of proven security solutions to support OT and IT managers.
These solutions, when deployed together, can help form an effective part of defense-in-depth strategies that maximize the ability of security managers to build effective protection for ICS and OT systems. Enabling oil and gas companies to more safely pursue the benefits of convergence between IT and OT creates opportunities for faster and more flexible decision making, improved operational efficiency, enhanced productivity, and lower costs.

JAMES CLARK is an executive manager at BAE Systems Applied Intelligence, where he is responsible for managing and delivering cyber security services to clients in the energy and utility sectors. Clark has significant experience within the industry, having served as an information technology consultant for various major systems integrators. Since 2000, he has focused mainly on the energy, utility and government sectors.

Geoffrey Graham is a business development solutions architect at BAE Systems Inc.’s intelligence and security sector, where he helps oil and gas companies leverage cutting-edge open-source analytics, cyber security, geospatial/mapping, and IT products to achieve their most demanding missions. Previously, Graham was a leader in executing large-scale software projects for another business.
For other great articles about exploration, drilling, completions and production, subscribe to The American Oil & Gas Reporter and bookmark www.aogr.com.